TARKOV-BITCOIN-FARMDIAGRAMMROBIN HOOD-BITCOIN-WALLET-ADRESSEWIE MAN BITCOIN GEGEN ECHTES GELD EINTAUSCHT
Introduction This post will be an attempt at visualizing some of the strategies used by attackers...

APPS, UM BITCOIN ZU VERDIENENBITCOIN-BETRUG BEI DATING-APPSBITCOIN FÜR ERWACHSENE
(Last edit: 2023-01-30 21:00, first version 2022-11-03 18:12) Summary of WhiteRabbit attack Ma...

AKZEPTIERTE BITCOIN-AKTIENMR BEAST PROMO-CODE BITCOINSTAKE-BITCOIN-GESETZE
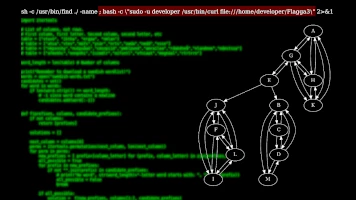
Finally back to a classic FRA challenge. This one turned out to be more of a programming/engineering...

ZITATE VON ANTHONY POMPLIANO ZU BITCOINKIND ZAHLT FÜR ELTERN-BITCOINBITCOIN-BÖRSE
Updated: 2022-10-23. (I first wrote the intro back in 2020 when this was active but I didn't want to...
AMAZON INVESTIERT IN BITCOINICH TEILE BITCOIN ETFVORHERSAGE DES BITCOIN-CHARTS
As I was "casually" surfing the web I stumbled upon some PHP files with random names. It turns out t...

BITCOIN RODNEY NETTOVERMÖGENBITCOIN-EREIGNISSE 2024ARLP-BITCOIN
This is just a short story of how I set up a honeypot and waited 10 months for a single request. And...
5X VERGOLDETE BITCOINSAPPLE KAUFTE 2,5 MILLIARDEN BITCOINWARUM BITCOINS
Intro This year our friends at FRA did something new and hosted a sort of Christmas crafts compet...
ANONYMITÄT VON BITCOIN-TRANSAKTIONEN M枚SERPENSIONSFONDS-BITCOINASROCK H81 BITCOIN
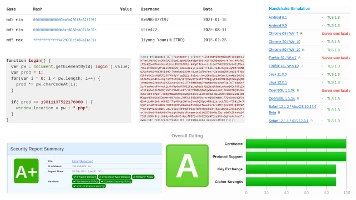
I just wanted to share some updates here on my website! :) New real security challenges I've s...
MICHAEL MANCIL BROWN BITCOINBITCOIN-FILM NETFLIXDER NIEDRIGSTE BITCOIN-PREIS
For more than 3 years "The famous HASH game" has been unavailable but now I'm happy to announce that...

BITCOIN-WALLET-APPBITCOIN-MINER UND NVIDIA AI CLOUD-PARTNERANONYME IOS-BITCOIN-WALLET
You're out surfing the world wide web having a great time, then suddenly, you find a security vuln...
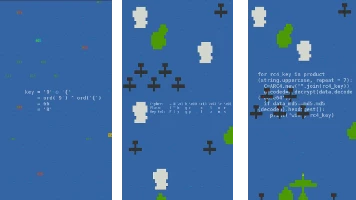
0,00002141 BITCOINANDROID-BITCOIN-MALWAREARGUMENTE FÜR UND GEGEN BITCOIN
In this post we continue on the topic of FRA challenges. This challengemirror is quite different f...

10 DOLLAR IN BITCOINEFT-BITCOIN-NEUIGKEITENBITCOIN-PREISKONVERTER
It's the end of the year and a nice time to look at the security challenges posed by our Swedish S...
BITCOIN-ERSTELLUNGRUSSLAND UND DIE USA WÄRMEN SICH AUF BITCOIN AUF0,19177215 BITCOIN IN USD
Greed is good, or is it? Cue the Vsauce intro. Have you ever thought, "How does the Internet w...
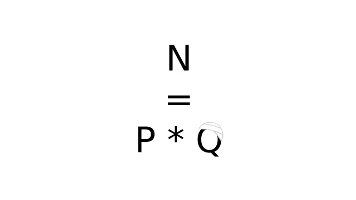
ZEITPLAN FÜR DIE TRUMP-BITCOIN-KONFERENZBITCOIN IM JAHR 2020WANN SPRICHT TRUMP AUF DER BITCOIN-KONFERENZ?
You have probably heard about backdoors in different software, the dlink user-agent backdoor[1] ...

0,0083686 0 BITCOIN10.000 BITCOINS FÜR EINE PIZZA1PASSWORT BLOCKIERT BITCOIN-MINER
Checksums and hashes are great for detecting errors and modifications of data, but what if your data...

0,03 BITCOIN ZU EUROBITCOIN-RECHNER IN USDERSCHEINEN VON BITCOIN
Most apps on your phone can interact with the Internet. By analysing the details of these interactio...

AKTUELLER BITCOIN-UNTERSTÜTZUNGSPREISACAHT BITCOINBITCOIN-APP
Why is no one using anonymous comments anymore? Either you have to register for yet another site or ...

REGISTRIEREN SIE SICH UND ERHALTEN SIE KOSTENLOSE BITCOINSANNAHMEN FÜR ERZWUNGENE BITCOIN-ÜBERWEISUNGENAMAZON NEUE BITCOIN
A few weeks ago my girlfriend showed me that the gym she goes to had started to upload instruct...
